By Jamie Ridenhour
The idea of creating a single point of operational information for security managers, field resources and clients has been around for quite a while, but is now truly possible with recent advances in connectivity. Security Force Management refers to applications that make upstream and downstream information sharing across a security program from frontline staff to back end management efficient, effective, and timely.
Using technology to manage security officers has been around for decades. Some of the first computerized systems appeared in the 1980’s with handheld data loggers and RFID sensors that in some instances continue to be used today. The systems track or log an officer’s patrol route to make sure appropriate rounds are made and checkpoints are visited.
While older systems like this are effective for tracking officer movements, the data they provide is limited and cumbersome to access. The data must be analyzed and distributed, most likely on paper reports, or office software before it is seen by those who need it most.
The major advancement, like so many things in our daily lives, came with the advent of powerful and connected mobile devices like smartphones and tablets. Developers of security force management applications have utilized the new technology to create systems that not only track an officer’s movements but provide a wealth of additional information and integrated documentation such as logs and reports as well. The inherent connectivity allows managers and clients to be able to conveniently and effectively view security officer activity and documentation.
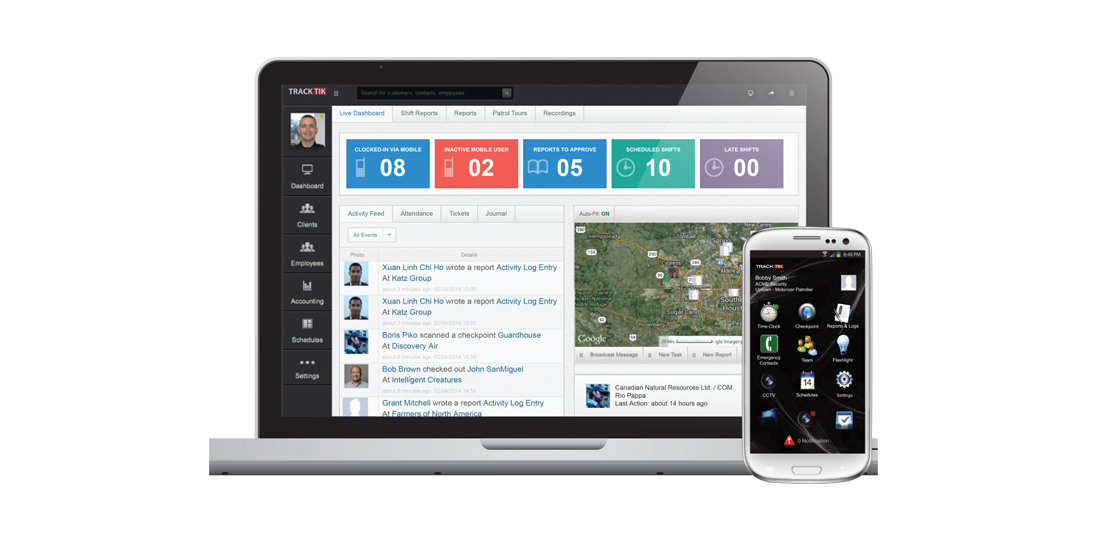
While on patrol, an officer can take photos or record sound and video if an event occurs or something simply seems out of place. These records are shared on a centralized system where they can be immediately accessed by management and clients. It is a level of insight and logging that has not been seen before. Quite simply, the systems provide a level of communication unthought of in the days of logbooks, notes, and paper notice boards.
Simplicity and ease of use are primary goals when these systems are developed. Relevant and comprehensive information is the desired result, but if the system is too difficult to use, the data will not be effectively captured. Even worse, time spent by an officer keeping logs and entering data is potentially time lost in providing security presence. Modern force management systems have been designed to be powerful, yet simple.
Ease of use is also important for managers and clients. As mentioned before, even the best data is of no value unless it is useful and accessible. The system dashboard in a force management application is made to address both needs. Force managers and supervisors as well as clients can easily access real time data along with weekly or monthly summaries. Each client can monitor their own account while the security provider has an overview of all accounts with the ability to drill down to specific information.
This brings us to perhaps the most important benefit of implementing a security force management system – transparency. The unprecedented level of access is valuable to the customer in that it lets them see exactly what their security service looks like. It also heightens their sense of security by demonstrating adequate coverage. These aspects hold true for the provider, as well. Supervisors can be confident that officers are doing their duty while account managers now have a valuable tool for demonstrating the effectiveness of protection to the client.
At first glance, a security force management application may seem like a gimmick or just another application, but the real value is in the transparency, accountability, and efficiency created between all parties involved in the security partnership. Front line officers, supervisors, management and clients all can now have visibility into the performance, data, and metrics of the security solution.